Load Balancing is not only about balancing load based on any tool such as HA-proxy, Apache 2, Nginx etc. but can also be achieved with help of firewall setup. Setting up a good firewall is an essential step to take in securing any modern operating system. Most Linux distributions ship with a few different firewall tools that we can use to configure our firewalls. So, we would use IP-tables as the measure to perform both aspects together of security as well as balancing the Network load.
Ip-tables is a standard firewall included in most Linux distributions by default. It is actually a front end to the kernel-level net-filter hooks that can manipulate the Linux network stack. It works by matching each packet that crosses the networking interface against a set of rules to decide what to do. Ip-tables almost always comes pre-installed on any Linux distribution. To update/install it, just retrieve the ip-tables package:
sudo apt-get install iptables
Working of IP-tables
- The iptables firewall operates by comparing network traffic against a set of rules. The rules define the characteristics that a packet must have to match the rule, and the action that should be taken for matching packets.There are many options to establish which packets match a specific rule. You can match the packet protocol type, the source or destination address or port, the interface that is being used, its relation to previous packets, etc.
- When the defined pattern matches, the action that takes place is called a target. A target can be a final policy decision for the packet, such as accept, or drop. It can also be move the packet to a different chain for processing, or simply log the encounter. There are many options.These rules are organized into groups called chains. A chain is a set of rules that a packet is checked against sequentially. When the packet matches one of the rules, it executes the associated action and is not checked against the remaining rules in the chain.
- A user can create chains as needed. There are three chains defined by default. They are:
INPUT: This chain handles all packets that are addressed to your server.
OUTPUT: This chain contains rules for traffic created by your server.
FORWARD: This chain is used to deal with traffic destined for other servers that are not created on your server. This chain is basically a way to configure your server to route requests to other machines.
- Each chain can contain zero or more rules, and has a default policy. The policy determines what happens when a packet drops through all of the rules in the chain and does not match any rule. You can either drop the packet or accept the packet if no rules match.
Listing current rules
Ubuntu servers do not implement any restrictions by default, but for future reference, check the current iptable rules using the following command
sudo iptables -L
This will print out a list of three chains, input, forward and output, like the empty rules table example output below.
Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
- target: If a packet matches the rule, the target specifies what should be done with it. For example, a packet can be accepted, dropped, logged, or sent to another chain to be compared against more rules
- prot: The protocol, such as icmp, tcp, udp or all.
- opt: Rarely used, this column indicates IP options
- source: The source IP address or subnet of the traffic.
- destination: The destination IP address or subnet of the traffic.
TOPOLOGY of EXPERIMENT
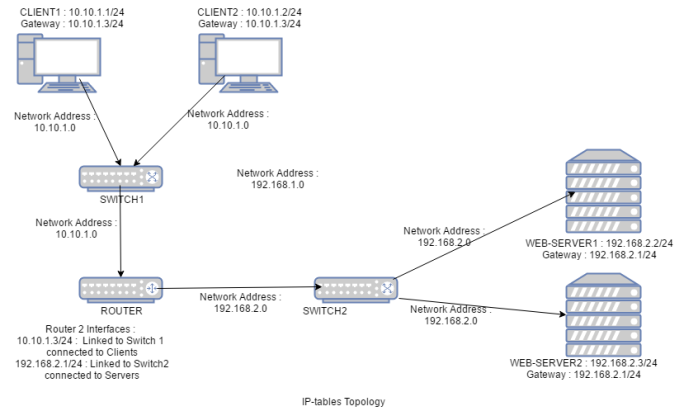
In the above topology, router needs to configured with the IP-table rules and should be configured so as to behave as a router.
sudo sysctl -w net.ipv4.ip_foraward = 1
Configuring IP-tables
Two ways have been used by us for providing rules of ip-tables. One method is based on the number of packets flown/transferred between clients and a particular server and the other is based on probabilistic note. Both ways are discussed below :
sudo iptables -t nat -A PREROUTING -p tcp -i eth1 --dport 80 -m state --state NEW -m statistic --mode nth --every 2 --packet 0 -j DNAT --to-destination 192.168.2.2:80 sudo iptables -t nat -A PREROUTING -p tcp -i eth1 --dport 80 -m state --state NEW -m statistic --mode nth --every 2 --packet 1 -j DNAT --to-destination 192.168.2.3:80
In the above configuration, PREROUTING is performed for a TCP packet on the eth1 interface [Note : eth1 interface is connected to the server side and not on the client side] with the destination port being 80 for the HTTP data-transfer to take place. As per our rule definition, every 2nd packet the server [from which response should arrive] is changing so, load is balanced and secured as no through the mentioned web-servers data can flow as per the rule and not through any other possible path.
sudo iptables -t nat -A PREROUTING -i eth1 -p tcp --dport 80 -m state --state NEW -m statistic --mode random --probability .50 -j DNAT --to-destination 192.168.2.2:80 sudo iptables -t nat -A PREROUTING -i eth1 -p tcp --dport 80 -m state --state NEW -m statistic --mode random --probability .50 -j DNAT --to-destination 192.168.2.3:80
This way of defining the ip-table rule is also pretty similar as the above one, only change being the flow depends on a random probability of the server responding to the request. So, in the above example we have chosen 50% probability of servers responding to the requests which is the case as a round-robin algorithm should be working.
Note that probability rules and the above mentioned can have different count of packets and probability distribution for the different rules and can make differences in how their load get’s balanced.
After configuring and adding up the rules, ip-table rules should be saved for their proper execution.
sudo iptables-save
TESTING and OBSERVATIONS
- Manually configure all the IP addresses of clients, servers and the router.
- Once the topology is set configure the router with the above steps.
- Run wire-shark in the clients so as to know from where the response is coming.
- Access from the browser the .php file created embedded with 10 HTTP objects as:
192.168.2.1/file.php [From any browser] curl http://192.168.2.1/file.php [From terminal]
- Notice the wire-shark captures attached and analyze the requests handled by the server in the manner ip-tables were configured.
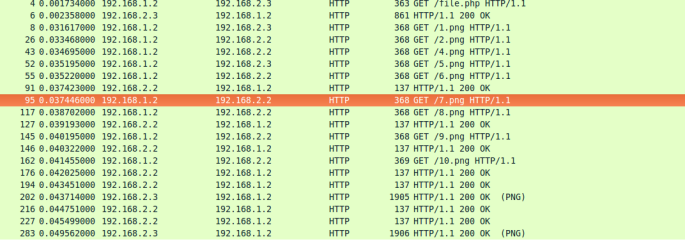 Fig : Capture using IP-tables based on Number of packet requests.
Fig : Capture using IP-tables based on Number of packet requests.
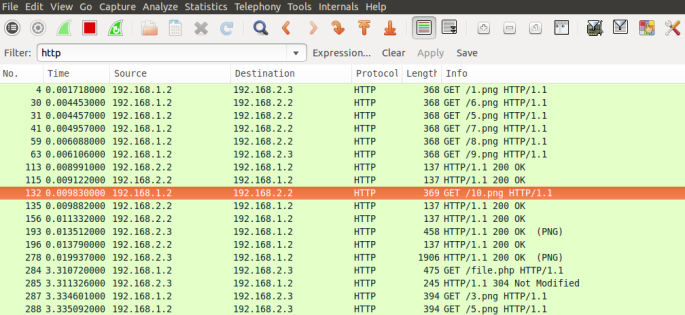 Fig : Capture using IP-tables based on random Probability.
Fig : Capture using IP-tables based on random Probability.
FLUSHING IP-Tables
Once all work is done and packets have been analyzed then it’s really important to flush or delete the ip-table entries as rules meant to redirect traffic every time based on ip-tables and not on any other criteria. Also, if some errors arrive while working do flush the ip-table entries and then configure again. Below commands can be combined as a .sh file and be executed for flushing/deleting the ip-table entries.
sudo iptables -F sudo iptables -X sudo iptables -t nat -F sudo iptables -t nat -X sudo iptables -t mangle -F sudo iptables -t mangle -X sudo iptables -P INPUT ACCEPT sudo iptables -P FORWARD ACCEPT sudo iptables -P OUTPUT ACCEPT sudo iptables -t raw -F sudo iptables -t raw -X
Hope you enjoyed working with IP-tables:). We would like to hear feedback on the experiment and ask you to see our other tutorials. Thanks a lot for reading the tutorial.